top of page

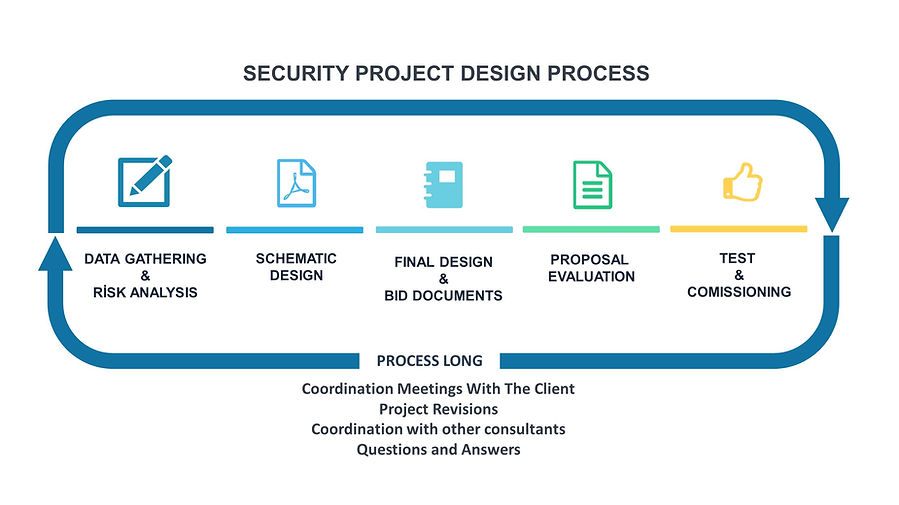
Security Project Design
-
As in all processes, a security system design starts with a Risk Analysis, during which;
-
The project is analyzed with its environmental factors and their effects on the risks
-
The architectural project is reviewed with its potential effects on risks and the security concept to be developed
-
The planned vehicle and pedestrian access ways are analyzed with the effects on the risks and the security concept to be developed.
-
-
Following the Risk Analysis, the Security Concept Report, which involves details regarding the risk analysis and mitigation recommendations, the recommended security concept, is issued for Client approval.

-
Following the approval of the security concept by the client, the recommended system is placed on the architectural drawings in ACAD format. Every single equipment, at all sizes and functions are placed in Schematic Design and presented to the client for approval
-
Following the approval of the Schematic Design, the Final Design and Bid Documents are issued;
-
All the equipments within the system are placed on ACAD Drawings, given unique codes. All equipments that may require space are scaled to the project. The drawings are issued in ACAD and PDF formats.
-
All and each equipments are listed in Equipment Tables with their unique codes. Any equipment which will operate in integration with another equipment will be referred to in this table. So the installer will know which equipment will need to be integrated with which other equipment.
-
BoQ list involves the list and quantites of hardware and software types to be used in the project
-
Technical Specifications, prepared uniquely for the project, details the minimum technical requirements of all hardware and software to be used in the system, as well bidding requirements such as, required standards, proposal formats, mobilization plans.
-
-
bottom of page